 As 2-factor authentication (2FA) and multifactor authentication (MFA) continue to improve in scope, scale and performance, greater reliance is being placed on security at the edge of the network (i.e. the user and the device). When it comes to the user, a commonly bandied phrase is that ‘the user is the ultimate security perimeter’ – which is especially true in the PIN/password regime where users are burdened with having to comply with complex password policies. These are made even more difficult when used on mobile keyboards, often too tiny and extremely cumbersome to get to numbers and special characters.
As 2-factor authentication (2FA) and multifactor authentication (MFA) continue to improve in scope, scale and performance, greater reliance is being placed on security at the edge of the network (i.e. the user and the device). When it comes to the user, a commonly bandied phrase is that ‘the user is the ultimate security perimeter’ – which is especially true in the PIN/password regime where users are burdened with having to comply with complex password policies. These are made even more difficult when used on mobile keyboards, often too tiny and extremely cumbersome to get to numbers and special characters.
Earlier this year, I wrote about the positive impact of emerging technologies, and the emergence of ‘4th Factor, Continuous’ Authentication, covering a fascinating range of behavioural, speech, finger, facial, physiological and voice-based methods for context-aware, risk-based and dare-I-say “friction free” authentication. These modalities offer promise of zero-effort-authentication for the user, at very high levels of security.
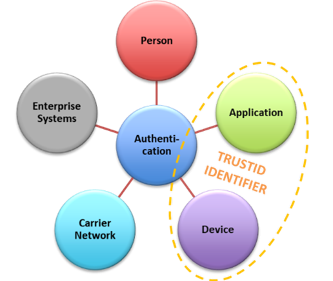
While device and network-based authentication tools have been around for many years, there has been a notable improvement in performance more recently through the use of sophisticated machine learning algorithms on an ever-increasing set of data from a variety of sources that include on-device sensors (microphones, DTMF/Tone key generators, SIM libraries etc). In that context, caller authentication services provider TRUSTID has launched its IDENTIFIER product, with patented network forensic technology, available “as-a-Service” for easy combination with other security modalities.
Network and device “printing” are effective in digital and contact center channels. When it comes to mobile-only, the service may be used in combination with other on-device capabilities that users are self-adopting with greater ease, such as Apple’s TouchID, FaceID and Samsung’s Intelligent Scan. For contact centrer, the service may be integrated for pre-call screening within the IVR, and before or even during calls with live and virtual agents.
Categories: Conversational Intelligence, Intelligent Authentication, Articles

 Getting It Right: What AI Agents Actually Mean for Customer Support (Webinar)
Getting It Right: What AI Agents Actually Mean for Customer Support (Webinar)  Beyond the Basics: How AI Is Transforming B2B Sales at TP
Beyond the Basics: How AI Is Transforming B2B Sales at TP  Voice AI Agents Redefine CX: Trends, ROI, and Strategies for 2025
Voice AI Agents Redefine CX: Trends, ROI, and Strategies for 2025  Why Voice AI Is Foundational for Enterprise Innovation (Webinar)
Why Voice AI Is Foundational for Enterprise Innovation (Webinar)