[Today, Opus Research released its latest report and forecast of voice biometric technologies and solutions: “Voice Biometrics 2009: Building on Expectations.” Below is a brief excerpt that addresses the overall objective of voice biometric technologies in customer care settings.]
One of the banes of phone-based commerce is the phrase, “Your call is important to us.” It tends to be the last thing an inbound customer hears from an IVR system before being put on interminable hold. It would be much more reassuring – and accurate – for an IVR to say that “Your identity is very important to us” and then, rather than indiscriminately placing each call on hold, to treat each caller according to his or her expressed preferences, status, or other known attributes.
Both businesses and technology providers repeatedly affirm that “caller experience is of paramount importance.” Yet, that does not mean that they place risk management or security in a lesser role. They recognize that speaker verification provides a mechanism to serve these seemingly contradictory goals – highly usable, highly secure interactions.
For too long the most common practice for handling inbound calls was to put even their best customers through onerous question-and-answer routines to validate their identity based on “knowledge-based authentication.” While it is deemed “good enough,” it is neither customer-friendly (because it takes so long), nor particularly secure (because the information is often available through a number of physical or online sources).
Instead of making the spurious claim that “your call is important to us,” leading-edge service providers, like Australia’s largest healthcare specialist ahm (Australia Health Management), and one of its top banks (National Australia Bank) are showing customers in practice that “your identity is important to us.” Their use cases are “inclusive,” meaning that the use of speaker verification addresses both UI and security concerns, providing a “win-win” for customer and company alike. Both recognize that quick, accurate authentication is beneficial to the customers as well as to the business enterprise.
Strong Authentication Raises Confidence
As the number of customer-facing voice verification implementations grows, enterprises and their technology providers have already learned the value of strong caller authentication. They’ve also learned that voice biometric authentication never exists in a vacuum. Low levels of confidence in a voice biometric match seldom leads to outright rejection of a call. Instead, they trigger routines to obtain other information that can include CallerID or ANI (automated number identification) as well as “risk profiles” based on customer records, transaction history, “last known location” and the like.
Voice biometric-based authentication can replace or augment the entry of the caller’s account number. When the captured utterance matches a stored voiceprint, the authentication engine returns a high-confidence indicator (“green light”). If there are no other concerns, the caller can proceed toward accomplishing the purpose of the call.
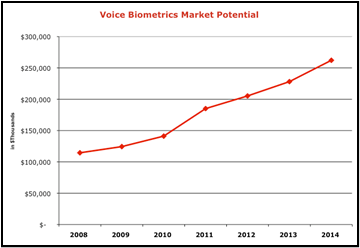
As for market potential, Opus Research sees global spending on Voice Biometrics-based solutions (a category that goes far beyond customer care to include automated password reset, remote “time and attendance” reporting, voice signatures, mobile security and the like) reaching about $124 million in 2009 and growing to roughly $260 million in 2014 (roughly 16% compounded annual growth rate).
The biggest challenge is developing expeditious call flows for handling calls which, for any number of reasons, might fall into one or more gray areas in user authentication. Perhaps the risk profile is high and the call originates from a noisy environment. Automated, phone-based authentication could be difficult. Businesses, and their technology providers, must also build the business logic to govern situations where there is a strong match to the voice biometric, but the risk management system calls for additional authentication based on other metadata (such as a report of a lost payment card).
Solutions providers offer a considerable number of options to deal with the instances where other resources (such as the risk management system) yield a “yellow,” or worse “red” light. Calls may originate from unknown devices, in unexpected geographic locations. The voice biometric may indicate strong confidence in the caller’s identity, but he or she may not remember a pass-phrase or know the actual response to a wallet-based query. (How many of us can accurately answer, “What was the exact amount of your last purchase at a bar or eating establishment?”) Companies have considerable leeway in designing call flows and agent scripts for these instances.
A well-designed authentication routine will minimize the instances that require lengthy, agent-based authentication. Experience in the field is helping to establish “best practices” for dealing with those “caution light” situations when a caller cannot be totally rejected, nor can a company readily allow them access them to sensitive information or personal funds. Agents have important roles to play in establishing caller expectation and, in essence, training them to use the system. They may end up resorting to KBA (knowledge-based authentication) but they will be able to explain to the customer why they are being subjected to further questioning.
The customer care pendulum is swinging away from a short list of company-driven choices toward a wide-range of customer-defined interactions and transactions. Rapid recognition and protection of a caller’s identity and associated information is the basis of higher quality customer care. Over the phone, deployment of voice biometric-based identity proofing can make such authentication simpler, faster and more pleasant. A growing body of “real world” experience shows that voice biometrics streamline the authentication process and lead to shorter calls which are more economical for the company and a better experience for the caller.
Categories: Articles

 2025 Conversational AI Intelliview: Decision-Makers Guide to Self-Service & Enterprise Intelligent Assistants
2025 Conversational AI Intelliview: Decision-Makers Guide to Self-Service & Enterprise Intelligent Assistants  Why Is ElevenLabs Building a Conversational AI Stack?
Why Is ElevenLabs Building a Conversational AI Stack?  Talk to the Web: How NLWeb Opens Conversational Access to Site Content
Talk to the Web: How NLWeb Opens Conversational Access to Site Content  Battling ‘Botenfreude’: The Power of People and Policy
Battling ‘Botenfreude’: The Power of People and Policy